Updated samples indicate access to original source code and active development, signaling that GOLD SOUTHFIELD has resumed operations. Monday, May 9, 2022 By: Counter Threat Unit Research Team
Secureworks® Counter Threat Unit™ (CTU) researchers analyzed REvil ransomware samples that were uploaded to the VirusTotal analysis service after the GOLD SOUTHFIELD threat group’s infrastructure resumed activity in April 2022. The infrastructure had been shuttered since October 2021. Analysis of these samples indicates that the developer has access to REvil’s source code, reinforcing the likelihood that the threat group has reemerged. The identification of multiple samples containing different modifications and the lack of an official new version indicate that REvil is under active development.
The March 22 sample contains artifacts in its configuration that indicate a likely link to a victim published to the REvil leak site in April. Despite a version value of 1.00, the sample has a compile timestamp of 2022-03-11 14:30:49 and includes functionality from a version 2.08 sample identified by CTU™ researchers in October 2021. The March 2022 sample includes the following modifications that distinguish it from the October 2021 sample:
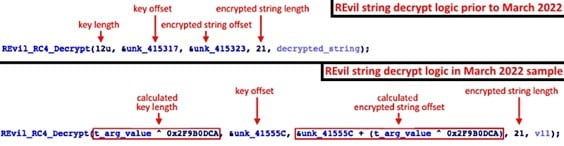
- Updates string decryption logic to rely on new command-line argument: A change to the string decryption logic impacts REvil’s ability to successfully execute. To run successfully, the threat actor must provide REvil with a pre-determined four-byte integer value between 0 and 4294967295 (0xFFFFFFFF). REvil uses this value during the string decryption process to calculate the RC4 decryption key length and the encrypted string offset. Prior REvil samples used hard-coded lengths and offset references. Figure 1 shows a comparison between the original logic and the logic implemented in the March 2022 sample.
Figure 1. String decrypt logic changes in the March 2022 sample. (Source: Secureworks)This value is passed to the REvil executable via a new “-t” command-line argument. Failure to provide the argument and the correct value results in the executable’s termination. Without the correct value, REvil cannot decrypt essential strings such as library and function names that are dynamically resolved at runtime. While this feature prevents network defenders from detonating the REvil sample in a sandbox environment if they do not know the pre-defined value, the unique command-line pattern could make the samples easier to detect and block.
CTU researchers determined that the integer value for the March 2022 sample shown in Figure 1 is 798690758 (e.g., “<REvil executable filename> -t=798690758″). The REvil code applies a bitwise XOR operation to the hex equivalent of 798690758 (0x2F9B0DC6) and the hard-coded value 0x2F9B0DCA, resulting in a calculated key length of 12. Because the key offset is known (0x41555C), the RC4 key and encrypted data can be extracted and processed using this calculated key length. Figure 2 shows an encrypted string structure in the March 2022 sample that starts with the RC4 key (EF916A059DD98FC8B3AC6747) followed by an encrypted string at the calculated offset (BB17AD3083FA3A84D943F1F6F3F3DD1891F544EC5D) that decrypts to CreateStreamOnHGlobal.
Figure 2. Encrypted string storage structure at calculated offset. (Source: Secureworks) - Updates hard-coded public keys: The malware author changed the two 32-byte hard-coded public keys used to secure artifacts compiled during the encryption session. GOLD SOUTHFIELD may have lost access to the original private key pairs, or those keys may have been exposed. The first key is stored at the start of the sample’s .data section at offset 0x10. This key is used to encrypt the session’s private key, which is generated at runtime and used to encrypt files. The ASCII representation of this key is 83449D3C46A7946EA2E130C46EE88D6933DD3F9E3CDCAC9E8EB42792F713F60A. The second key is stored in the sample’s .data section at offset 0x30. This key is used to encrypt the “stats” JSON data that contains information about the encryption session (e.g., affiliate tracking information, encrypted session private key, victim’s username, system’s locale, drive details). The ASCII representation of this key is 84A44FF8FAC498117B469EE8AE2A33A67308E0192A5650FF0501482A3B03BE15.
- Changes the configuration storage location: The encrypted configuration structure is stored at offset 0x50 relative to the start of the sample’s .data section. The decryption key stored at the start of this offset consists of 32 bytes ranging from 0x00 to 0xFF (see Figure 3).
Figure 3. Configuration storage location in the March 2022 REvil sample. (Source: Secureworks)Prior REvil versions stored the configuration structure at the start of the section (offset 0x00). In most cases, the structure was stored within a non-standard section (e.g., .kjmxo0e). The key in prior versions was limited to alphanumeric characters (e.g., gobpsd6RudAzmGciEytyLAjeGAk5H8Yd) as opposed to any byte value.
The overall configuration structure remains unchanged. It contains the decryption key (32 bytes), the precalculated CRC32 hash of the encrypted configuration (4 bytes), the encrypted configuration data length (4 bytes), and the RC4-encrypted configuration data.
- Changes affiliate tracking data format: When first introduced, REvil’s affiliate tracking “pid” and “sub” values were stored as integers within the configuration. In February 2020, GOLD SOUTHFIELD started using bcrypt to hash these values to prevent researchers from tracking affiliates. The March 2022 sample changed the pid and sub value format to a globally unique identifier (GUID). The analyzed sample includes the following pid and sub values in its configuration:
- pid: b78ad33f-32e9-4756-8c7b-83d46f8a0e19
- sub: bb9ced79-3e79-4649-8fcc-3d4295fabc08
The pid configuration element is never used, as the function that processed this configuration element was removed from the codebase. The only reference to the pid value was replaced with a duplicate sub reference (see Figure 4).
Figure 4. Comparison of stats data showing replacement of pid variable with duplicate sub variable in March 2022 sample. (Source: Secureworks) - Removes prohibited region check: The October 2021 REvil sample removed code that verified the ransomware was not executing on a system that resided within a prohibited region. This removal enabled REvil to execute on any system regardless of its location. The isProhibitedRegion variable that was assigned the result of this check was still present in the code but was assigned a hard-coded value of “false” (see Figure 5).
Figure 5. Prohibited region variable assigned hard-coded value of false in October 2021 sample. (Source: Secureworks)The March 2022 sample removes this variable and no longer includes it in the stats data.
- Leverages “accs” configuration element: The accs configuration element introduced in the October 2021 sample did not contain a value, but CTU researchers determined that it should contain a list of strings that represent username and password combinations separated by the percent (“%”) sign. If this value is defined, the ransomware uses the credentials to attempt authentication to protected network resources prior to encrypting their contents. However, it was unclear if the threat actor intended to list common username and password combinations or include credentials extracted from the targeted environment.
The March 2022 sample includes values in the accs configuration element, and the credentials appear to be targeted. Most of the credentials were for specific administrative accounts (see Figure 6). A typo in one of the credentials (“5” instead of “%”) suggests that the threat actors may manually format the values before including them in the configuration.
Figure 6. Targeted credentials listed in the accs configuration element of the March 2022 sample. (Source: Secureworks) - Includes new Tor domains in ransom note: The ransom note dropped on a victim’s system (see Figure 7) was updated to reference Tor domains that became active on April 19, 2022 when GOLD SOUTHFIELD’s infrastructure resumed activity:
- REvil leak site: blogxxu75w63ujqarv476otld7cyjkq4yoswzt4ijadkjwvg3vrvd5yd . onion
- REvil ransom payment site: landxxeaf2hoyl2jvcwuazypt6imcsbmhb7kx3x33yhparvtmkatpaad . onion
Figure 7. REvil ransom note containing updated Tor domains for payment and leak sites. (Source: Secureworks) - Changes safe-mode option values: The March 2022 sample modified safe-mode reboot details:
- The password for the current user was set to “k$UqZy9zIC”.
- The RunOnce registry values used for post-reboot operations were set to “*AqfNn6” and “*SrTITZ” (see Figure 8).
Figure 8. Updated RunOnce registry values associated with REvil’s safe-mode reboot. (Source: Secureworks)
- Updates registry key and values: The registry key that stores encryption-related information was set to SOFTWARE\JnX5ywJ. The value names stored within this key also changed, which is consistent with the author’s pattern of renaming registry values in each version. Table 1 lists the registry values in the March 2022 sample.
Registry Value Purpose 3OG Threat actor’s public key in REvil’s configuration b2vr Session public key Elnzo Session private key encrypted with the threat actor’s public key in REvil’s configuration 16uKrF7 Random extension generated at runtime and appended to encrypted files E7w3RRdi Encrypted ‘stat’ JSON data structure that contains information about the system and the malware Table 1. REvil registry values used to store encryption data in the analyzed March 2022 sample.
On April 29, 2022, Twitter user @JakubKroustek detected a REvil sample with a compile timestamp of 2022-04-26 19:39:04 and a version value of 1.00. CTU analysis of the April 2022 sample revealed that its functionality is nearly identical to the March 2022 sample. However, the April 2022 sample does not contain the string decryption changes implemented in the March 2022 sample.
Third-party reporting claimed that the April 2022 sample did not encrypt files but instead renamed them to a random extension. CTU researchers determined that a bug caused this behavior. The malware author modified the functionality that renames files being encrypted. The bug resides within a test that determines if the file rename operation was successful (see Figure 9, line 13).
Figure 9. Code associated with file rename bug preventing file encryption in April 2022 sample. (Source: Secureworks)
Because the malware author used “if ( !result )” instead of “if ( result )”, the file is successfully renamed on the first loop iteration but never breaks out of the loop. On the second loop iteration, the source file is missing because it has been renamed. As a result, the second file rename attempt fails and the file is never encrypted.
To mitigate exposure to this threat, CTU researchers recommend that organizations use available controls to review and restrict access using the indicators listed in Table 2. The domains may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
| db2401798c8b41b0d5728e5b6bbb94cf | MD5 hash | March 2022 REvil sample |
| 6620f5647a14e543d14d447ee2bd7fecc03be882 | SHA1 hash | March 2022 REvil sample |
| 861e2544ddb9739d79b265aab1e327d11617bc9d 9c94bc5b35282c33fcb419bc |
SHA256 hash | March 2022 REvil sample |
| ad49374e3c72613023fe420f0d6010d9 | MD5 hash | April 2022 REvil sample |
| eb563ab4caca7e19bdeee807b025ab2d54e23624 | SHA1 hash | April 2022 REvil sample |
| 0c10cf1b1640c9c845080f460ee69392bfaac981a4 407b607e8e30d2ddf903e8 |
SHA256 hash | April 2022 REvil sample |
| blogxxu75w63ujqarv476otld7cyjkq4yoswzt4ijadk jwvg3vrvd5yd.onion |
Domain name | REvil leak site in April 2022 |
| landxxeaf2hoyl2jvcwuazypt6imcsbmhb7kx3x33yh parvtmkatpaad.onion |
Domain name | REvil ransom payment site in April 2022 |
Table 2. Indicators for this threat.
To learn more about how ransomware groups adapt, read our Ransomware Evolution analysis and watch our Ransomware Trends: The Evolution of Threat webinar.
If you need urgent assistance with an incident, contact the Secureworks Incident Response team.
originally published onhttps://www.secureworks.com/blog/revil-development-adds-confidence-about-gold-southfield-reemergence