XDR’s compelling core value proposition is stopping threat actors in their tracks as soon as possible—even after they’ve penetrated your perimeter defenses. You need this capability because nobody’s perimeter is 100% impenetrable. It’s just the reality of the ongoing cybersecurity battle: at some point, you’re going to leave an internet-facing system somewhere unpatched, have a user fall for a phishing scam, or some other unfortunate event.
When that intrusion inevitably occurs, it’s absolutely imperative that you be able to quickly detect the malicious activity in your environment, identify the precise nature of that activity and take decisive steps to neutralize it—because every hour that a stealth attack goes undetected, it becomes more likely that your organization will suffer a catastrophic compromise.
Without XDR, threat actor dwell time can span weeks or even months as they surveil your environment and gain access to administrative rights, inching closer to your most precious digital assets. That’s because — unlike EDR, SIEM, or other previous cybersecurity technologies — only XDR can detect and correlate disparate clues from across your environment (including endpoints, network infrastructure and clouds) to quickly alert you to the presence and behaviors of an active invader.
The value of any XDR solution is therefore contingent upon how well it performs this identification and correlation. That’s why it’s vital for you to understand the specific advantages Taegis™ XDR offers when it comes to translating the massive data your environment generates – in various forms of relevant telemetry – into consistently and reliably faster detection of threat actors.
Those three advantages are:
Advantage #1: An unmatched knowledge base of current threat actor activity and techniques
Secureworks operates one of the most advanced threat intelligence operations in the world: our Counter Threat Unit™ (CTU) is comprised of more than 100 researchers with analytical access to more than 2.8 trillion events per week from across more than 4100 different client environments worldwide.
Our CTU™ team also has access to the results of more than 1400 incident response engagements annually — further adding to the total volume of empirical data we can leverage to make Taegis™ XDR the smartest threat detection platform in the world.
Advantage #2: Proven leadership in rapidly and continuously creating active threat detectors
It’s not enough to simply know what kinds of data likely indicate the presence of a threat actor. You also need to translate that knowledge into a corresponding “fingerprint detector” that can reliably identify exactly when a specific type of threat-actor fingerprint is present in an environment — without excessively generating false positives for that class of footprint.
This is a non-trivial skill set. The set of keystrokes a given threat group tends to use once it gets access to admin privileges for Office365, for example, will be similar — but not exactly identical — across all of its intrusions. It thus takes a special combination of experience, craft and institutional wisdom to turn captured forensic data into trustworthy forensic detectors. Here again, Secureworks’ superior skill set serves to differentiate Taegis™ XDR’s capabilities. In fact, we’ve developed and deployed over 18 thousand separate detectors which we continue to refine and enhance daily.
Advantage #3: Better algorithmic correlation of disparate detectors to ID the full active threat
To quickly and fully interdict an active threat before it reaches its goal, you have to do more than just identify a fingerprint here and there. You also have to logically correlate alerts from your disparate detectors to ascertain the true overall nature of your active threat scenario. Otherwise, you’ll just wind-up playing whack-a-mole with your intruder—reacting to individual symptoms of the attacks without curing your environment of the underlying problem.
To achieve this critical capability within Taegis™ XDR, Secureworks® constructed (and is continuously refining) a purpose-built set of algorithmic mechanisms, which we actively complement with indispensable human intelligence. We do not — as is the case with most of our competitors — simply apply the general principles of data science to the very idiosyncratic challenge of threat detection. Instead, we take advantage of our exclusive focus on cybersecurity to relentlessly optimize Taegis XDR’s ability to recognize the forest by linking all the trees.
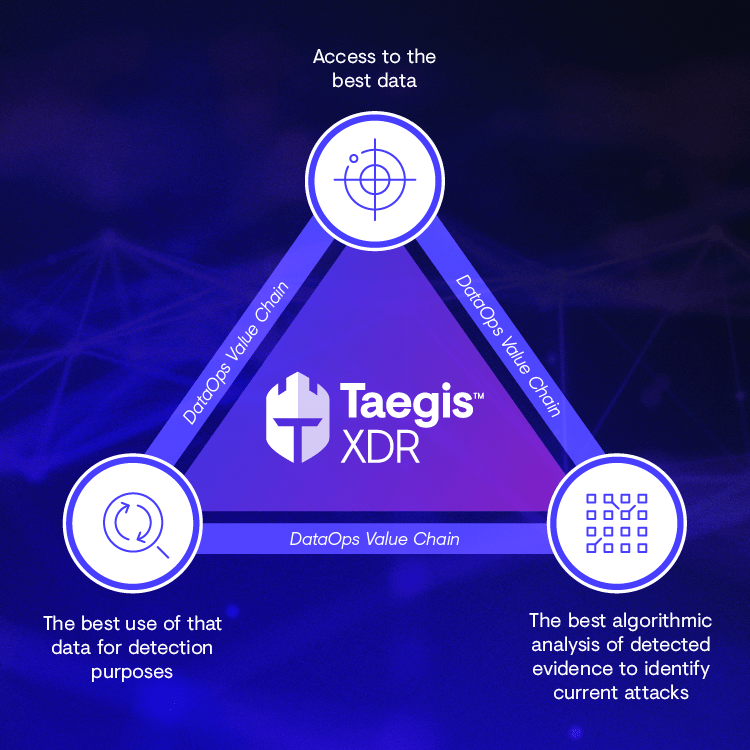
These three advantages — access to the best data, the best use of that data for detection purposes and the best algorithmic analysis of detected evidence to identify current attacks — form an end-to-end DataOps value chain that sets Taegis™ XDR from Secureworks’ competition.
Send Unwanted Intruders Packing with Taegis™ XDR™
More importantly, these differentiators optimize your ability to slash the dwell time of threat actors as they seek to do your organization harm.
Taegis™ XDR also offers you the added benefit of complementing your XDR implementation with best-in-class threat detection services from Secureworks or a Secureworks-certified partner. That way, you don’t have to be entirely dependent on your own internal SecOps skills to root out stealth intruders who may have gotten past your perimeter defenses.
For these reasons and others, I strongly encourage you to learn more about Taegis™ XDR. There’s no better way to turn state-of-the-art threat intelligence data into a powerful defense against active threats.
You Might Also Like
originally published onhttps://www.secureworks.com/blog/stop-playing-whack-a-mole-with-intruders-and-start-cutting-dwell-time-today