Technology shapes the way we interact with each other. More people than ever are working from home and utilizing mobile phones, laptops, and other devices to communicate. This reliance on and trust in communication technologies have prompted threat actors to increase phishing and smishing attacks, attempting to compromise personal and business devices. Access to just one device could enable a threat actor to compromise an entire network.
Working remotely may increase trusting behavior
In 1937, Howard Odum coined the phrase ‘technicways’ to express how behaviors change in response to technological and communication advancements. This behavioral study still applies to modern technology. Individuals are more likely to accept and respond to a text, ping, or poke than to write and send a physical letter or make a telephone call. However, trusting electronic communications without verifying the sender and the request can introduce considerable risks, especially in a business environment. As organizations shifted to a primarily remote workforce in response to the COVID-19 pandemic, employees began working from home and conducting all external interactions via remote communication solutions. The heavy reliance on electronic communications, the push to maintain “business as usual,” and the sense of security provided by the home setting may cause employees to be even more trusting of emails and texts.
Social engineering attacks are exploiting the remote culture
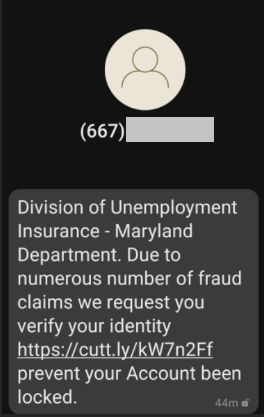
Threat actors have used phishing attacks for decades, but the content and format of the messages have become increasingly convincing. There has also been an increase in targeted phishing attacks (spearphishing) that are customized to the recipient. It is often difficult to distinguish a phishing email from a legitimate message. As the popularity of mobile phones and SMS messaging increased, threat actors expanded to smishing. These malicious text messages often prompt the recipient to perform a task that would authorize an action or divulge personal account information (see Figure 1).

Figure 1. Smishing attempt requesting personal information. (Source: Secureworks)
Coinciding with the increase in remote working, Secureworks® incident responders have observed an increase in smishing attacks that leverage CEO fraud. The threat actor impersonates a CEO and asks an employee to perform tasks such as making wire transfers or gift card purchases. Remote employees have been more likely to perform the fraudulent business task, likely because they cannot easily verify the request face-to-face in an office or by talking directly with their colleagues. They trust the message because it appears to be sent by someone they know. Threat actors are also exploiting the increased use of package delivery services by using delivery notification texts to convince victims to install malicious mobile applications.
Secureworks incident responders have also observed threat actors leveraging click fatigue to bypass multi-factor authentication (MFA). When repeatedly presented with the same request (e.g., a pop-up window prompting the user to ‘reauthenticate’ to their device), many users eventually comply with little thought to the request’s legitimacy. MFA is an important component of an organization’s security strategy, but it must be implemented properly. Otherwise, threat actors could circumvent it.
Employee education is critical
Organizations were forced to adapt quickly during the pandemic, and many did not have training and security measures in place to transition to a remote workforce. Threat actors have exploited these gaps and have become more creative in how they manipulate users to achieve their goals.
In addition to implementing endpoint detection and response solutions and requiring MFA, organizations must educate employees about how to recognize social engineering attempts and report suspicious activity. Employees should also know how to report and respond to a compromise. The National Institute of Standards and Technology (NIST) provides guidance on identifying and responding to phishing attacks, and this guidance can also apply to other social engineering attacks. Common identifying characteristics include spelling and grammar errors, and link destinations that do not match the displayed URL. Organizations should also train employees to validate requests before taking action, particularly if the requests involve monetary transactions or account adjustments. Verification should occur via a trusted channel that is different from the request (e.g., verifying an email message with a direct phone call).
Conclusion
Evolved ‘technicways’ and organizational reliance on communication technologies have amplified threat actors’ use of social engineering attacks such as phishing and smishing. In addition to implementing processes and security controls, it is important for organizations to educate users about these attacks. Fostering an environment where users question and verify requests, even from high-ranking executives, can be the determining factor in whether an attack is successful.
To learn more about other social engineering threats impacting organizations, read Ransoms Demanded for Hijacked Instagram Accounts.
Secureworks offers multiple services that help organizations address security concerns presented by a remote workforce. If you need urgent assistance with an incident, contact the Secureworks Incident Response team.
You might also be interested in
Social Engineering Tactics: Why LinkedIn is as Dangerous as it is Useful
originally published onhttps://www.secureworks.com/blog/social-engineering-types-and-the-risk-to-remote-workforces