Cybersecurity can really stress you out. You face a constant barrage of cyber threats that you have to stop. If you fail, your company could face devastating consequences like operational disruption and data and financial loss that could end up putting you out of business. Plus, there’s the potential for public shame and reputational damage.
A lot of the stress you experience at your job is caused by the sheer volume of alerts generated by your security monitoring tools. There are just so many of them! It’s not always clear which ones require your immediate attention – or which ones you can treat with lower priority.
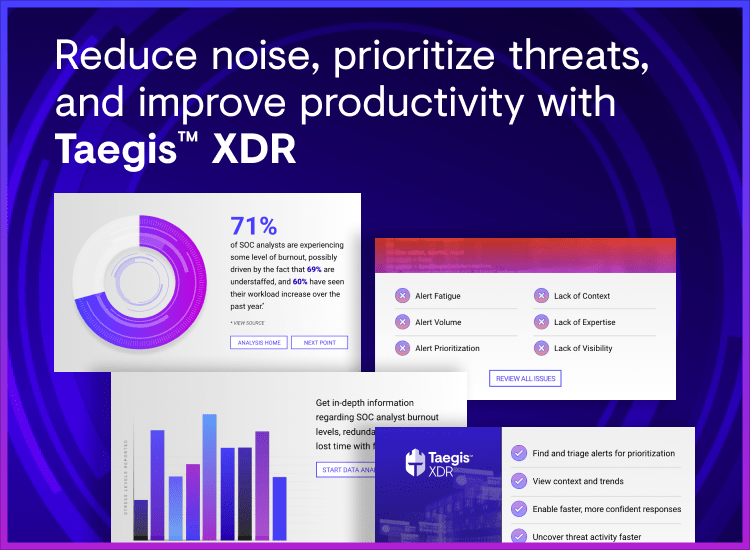
Worse yet, eventually you and your team may reach a point where the noise overwhelms the signal. When this happens, teams can start to burn out and lose focus. Research from ESG reveals that nearly half of daily alerts were ultimately determined to be false positives and 91% of organizations chose to run only in log or monitor mode, or turn their security tools off completely.1
This phenomenon is known as “alert fatigue.” And it’s common to many professions, from air traffic control to post-op nursing. As such, it’s a concept that has been closely studied for some time.
Based on those studies, it’s clear that SecOps teams need help with their cyber alert fatigue—and they need it fast. But when you’re drowning in content, it can be hard to know where to start. If you recognize the signs of alert fatigue, we recommend you start thinking about:
- Alert prioritization. If you spend less time dealing with false positives, you can get to real threats sooner. Alerts that have been automatically validated and prioritized tell you with high confidence which are most critical and help SecOps teams focus.
- Reasonable alert suppression. One of the best cures for alert fatigue is to keep trivial/innocuous alerts off your screen. You obviously don’t want to risk suppressing any alerts that may be meaningful. But with the right logic, you can significantly mitigate alert volume without compromising your team’s effectiveness.
- Unified security tools. Rather than having to swivel between multiple security tools, a centralized approach helps to eliminate operational complexities. By correlating security telemetry data across endpoint, network, cloud, and other business systems in one tool, security analysts can focus on the critical alerts occurring across their IT ecosystem through one console.
- Visualized alert data. Using charts, graphs, and real-time dashboards can help reduce noise and make it simple to spot anomalies that may indicate threat activity. You should customize dashboards to suit your own needs and quickly understand the true nature and context of an alert.
- Alert grouping. It shouldn’t take you an excessive amount of time to realize that 22 of your alerts are all essentially the same alert. Grouping alerts in bulk will do wonders for your alert fatigue. It will also help if you’re able to associate new alerts with previous historical alert groups.
- “Top Ten” lists. Your alert dashboard should help you find commonalities in your active alerts by highlighting relevant statistics about those alerts—such as “Top Ten” listings by source IP, target IP, and user.
- Bulk actions. It will also save you time and mental energy if you can act on a logical group of alerts by performing bulk actions on them—such as moving them all to an open investigation collectively, rather than one at a time.
Another important measure you can take against alert fatigue is to periodically assess how well you and your team are managing your alert workloads. Are you still getting a high volume of low-severity notifications? Is your untriaged alert queue getting longer or shorter? Was there a recent spike in alerts? How big was it? How well did your team cope with it?
By periodically reviewing these KPIs, you can make smarter decisions about alert management and resource allocation. A periodic review with your team is also a great antidote against that pernicious, burnout-inducing perception that work is just one constant onslaught of alerts. It’s a way to take a breath, review your performance, engender a sense of progress, and pat yourselves on the back for your successes.
Secureworks® is doing our part to help you avoid cyber alert fatigue by enhancing our XDR solution’s underlying logic and on-screen user experience. The new alerts experience makes it easier for users to see relevant alert information quickly, easily navigate through a large set of alerts, and prioritize the alerts that matter most. Additionally, users can now perform custom alert suppression, alert grouping, detailed alert search, and bulk action groups of similar alerts. You can read about the great new counter-fatigue features and functions we’ve added to our Taegis XDR solution here. And, of course, we welcome your suggestions about how we can make it even easier and less stressful to do your very demanding job.
As your organization keeps expanding its digital infrastructure, and as threat actors come up with even more ways to mess with your environment, the potential for greater alert volume—and therefore greater alert fatigue—will only increase. So make sure you give sufficient attention to the alert fatigue challenge. You can start by reading our white paper, Reduce Cyber Alert Fatigue in your IT Environment.
View our Infographic – Minimize the Noise of Cybersecurity Alerts
Sources:
1 ESG, Reaching the Tipping Point of Web Application and API Security
You Might Also Like
originally published onhttps://www.secureworks.com/blog/cyber-alert-fatigue-and-what-to-do-about-it